Introduction
This is the 4th box in the Tier 1 series. This machine touches the topics of redirects and bruteforcing a web login, similarly to its prequel preignition from Tier 0.
tl;dr
Spoiler!
1. Enumerate via dirbusting to find the login page.2. Edit the `/etc/hosts/` file to resolve to `ignition.htb`
3. Search for Magento default creds to login and get the flag.
4.

Establishing a Connection & Initial Scan
Spawn the bastard and get vpn going.
I’ve confirmed the target is reachable with a ping.
Start the default nmap scan and let it run while we complete the tasklist.
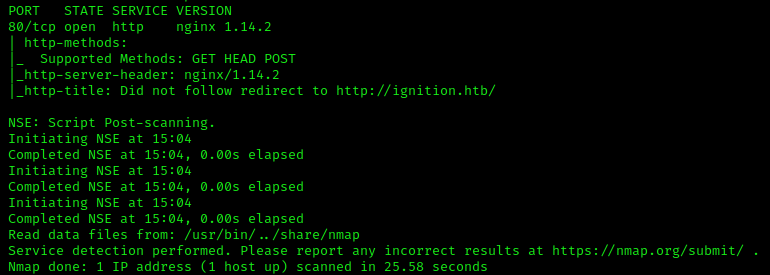
The Tasklist
Task 1
Which service version is found to be running on port 80?
Our scan above shows nginx 1.14.2 on port 80. This is a webserver, so there is a webpage we can visit via a browser.
Task 2
What is the 3-digit HTTP status code returned when you visit http://{machine IP}/?
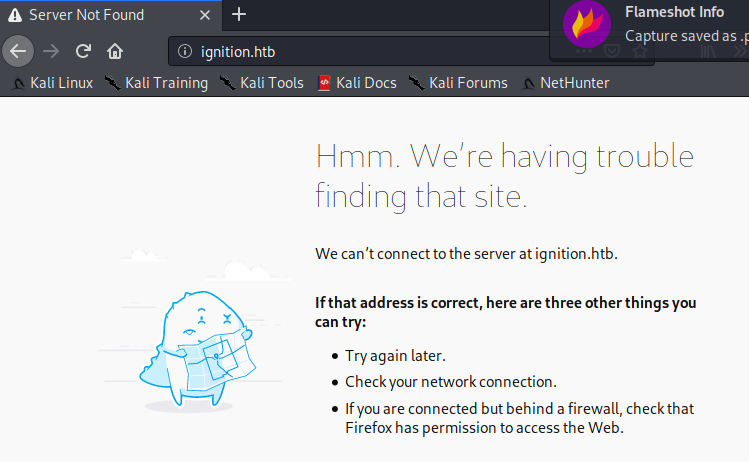
Well when we try to browse to the webpage, we get a Server Not Found error but I don’t see an error code.
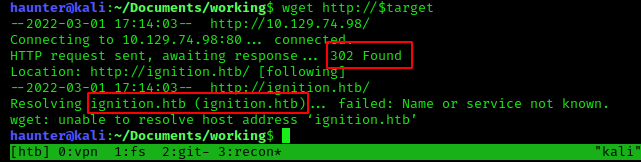
Using wget to fetch the page, however, does report back error code 302. According to this KB entry, this code indicates a redirect is in place.
Task 3
What is the virtual host name the webpage expects to be accessed by?
The same wget result shows ignition.htb is the host.
Task 4
What is the full path to the file on a Linux computer that holds a local list of domain name to IP address pairs?
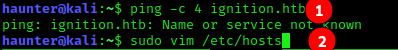
pingingthe host is unsuccessful. This can be fixed with the local hosts file.- The file is located at
/etc/hosts. We have tosudoin order to edit it.
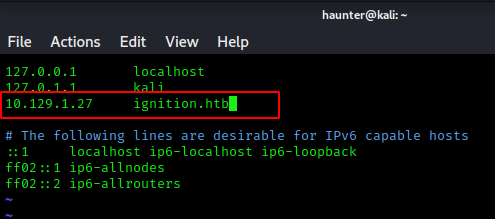
The target IP is paired with the ignition.htb on the same line.
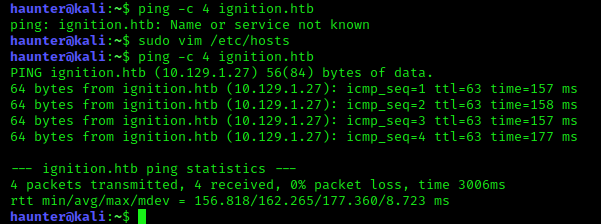
Once the changes are saved we can test the change by pinging again.
We can also now visit the site in-browser.
Task 5
What is the full URL to the Magento login page?
Let’s dirbust.
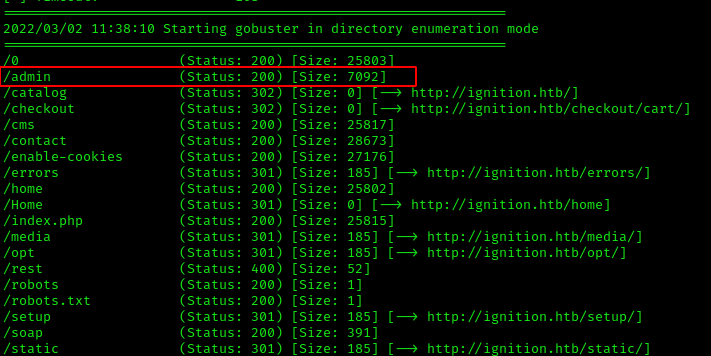
We found a directory called /admin.

Navigating to the directory in-browser redirects us to the Magento login page at http://ignition.htb/admin
Task 6
What password provides access as admin to Magento?
This part is a bit tricky. I tried using hydra to bruteforce the login, but they have account lockout enabled if bruteforcing is detected.

A manual bruteforce was successful after reading the Magento password requirements and narrowing down the list of passwords to use from a few different common password lists.
Task 7
Submit root flag
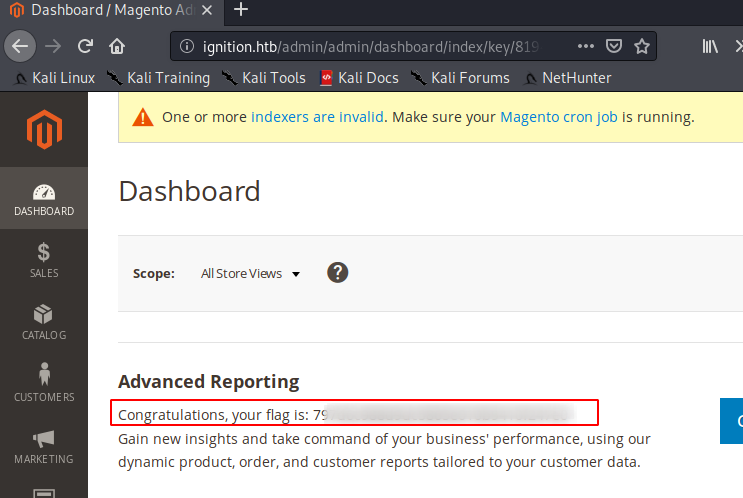
Once the correct password was found we got the flag.

Lessons Learned
- the
/etc/hostsfile can be edited to redirect our network traffic to a specific hostname

