Introduction
Reedemer is a new host on the Starting Point Tier 0 level. Some light reading of Redis will be needed for this exercise.
tl;dr
Spoiler!
1. Scan target. Redis is on TCP `6379`.2. Reference HackTricks [Redis](https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis#basic-information) page.
3. Install `redis-tools` if applicable. Connect with `redis-cli -h $target`
4. run `info` and look for the database that has keys (`db0`). `SELECT 0`
5. Enter `keys *` to show all the keys by name. Then `GET flag` to win.

Establishing a Connection
Spawn the bastard and get vpn going.
I’ve confirmed the target is reachable with a ping.
The Tasklist
Task 1
Which TCP port is open on the machine?
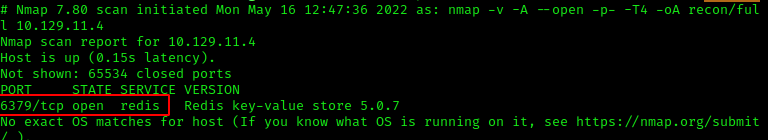
6379
Task 2
Which service is running on the port that is open on the machine?
The service is named redis according to our scan. 
Task 3
What type of database is Redis? Choose from the following options: (i) In-memory Database, (ii) Traditional Database
in-memory database
Task 4
Which command-line utility is used to interact with the Redis server? Enter the program name you would enter into the terminal without any arguments.
redis on HackTricks indicates we can use redis-cli.
Task 5
Which flag is used with the Redis command-line utility to specify the hostname?
I had to install the redis toolset. Use the following command if you need to do so as well: sudo apt-get install redis-tools
 You can then verify in the
You can then verify in the man page for redis-cli or the HackTricks article that the -h flag is needed to specify a hostname.
Task 6
Once connected to a Redis server, which command is used to obtain the information and statistics about the Redis server?
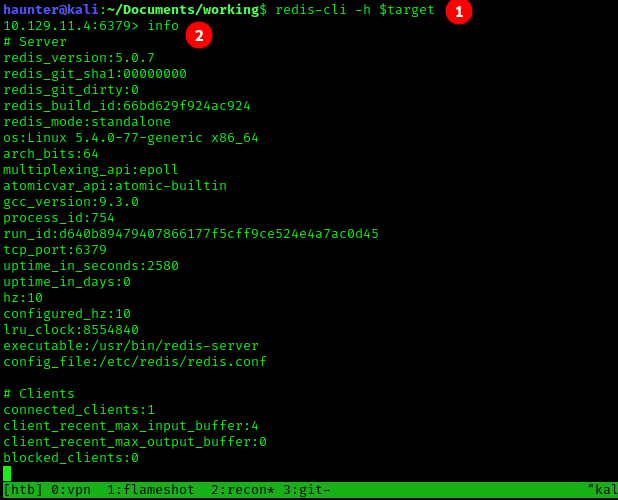
- We run the connection command
redis-cli -h $target - Once connected, I ran
info
Task 7
What is the version of the Redis server being used on the target machine?
5.0.7 according to the results of info we just ran.
Task 8
Which command is used to select the desired database in Redis?
SELECT
Task 9
How many keys are present inside the database with index 0?
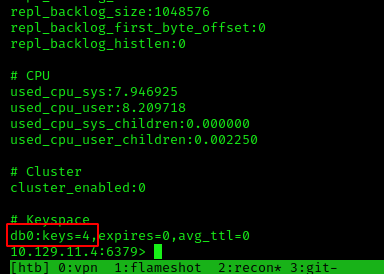 Scrolling through our results further, we see that there are
Scrolling through our results further, we see that there are 4 keys inside of db0.
We now can run SELECT 0 to query this database.
Task 10
Which command is used to obtain all the keys in a database?
keys *
Capturing the Flag
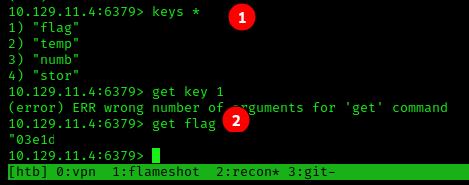
- Now that we have db0 currently selected, we can run
keys *to list everything it has. - Finally we use
get flagto show the value of the flag.

Lessons Learned
HackTricksis a great place to check for exploits/methodolog of services discovered from enumeration