Introduction
Preignition is the final box in the Tier 0 series, and the 2nd of 2 VIP machines. This lab focuses on web enumeration/dir busting.
tl;dr
Spoiler!
1. The target hosts a webserver. Use `gobuster dir -u $target -w [WORDLIST] -x php` to enumerate PHP webpages.2. `/admin.php` is found. Navigate to `$target/admin.php` in-browser.
3. Search teh googles for `nginx default admin password`. The default cred pair is `admin:admin`.
4. Login and retrieve the flag.
5.

Establishing a Connection & Initial Scan
Spawn the bastard and get vpn going.
I’ve confirmed the target is reachable with a ping.
As with all other labs to now, start a scan and let it cook while we do the boring task stuff.
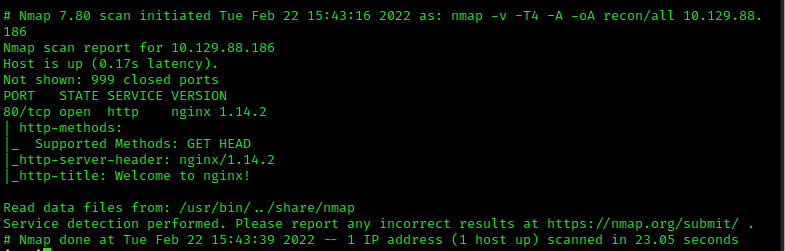
nmap -v -T4 -A -oA recon/all $target
The Tasklist
Task 1
What is considered to be one of the most essential skills to possess as a Penetration Tester?
The answer is dir busting, short for directory busting. This is an active recon technique that targets web servers with the intent of discovering directories/pages for potential exploitation.
Task 2
What switch do we use for nmap’s scan to specify that we want to perform version detection
man nmap shows us the following regarding version detection:
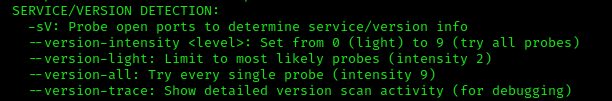
The switch in question is -sV.
Note: the
-Aswitch we have been using in our default scan includes version detection as well. However,-Acontains other utilities that may be overkill for targeted scans. In those instances, specifying-sVfor version detection would be more streamlined if that’s all that is needed.
Task 3
What service type is identified as running on port 80/tcp in our nmap scan?
Our results show http is running on 80/tcp.
Task 4
What service name and version of service is running on port 80/tcp in our nmap scan?
Results show the service name/version is nginx 1.14.2.
nginx is commonly used as a webserver solution. You can read moar about it here.
Task 5
What is a popular directory busting tool we can use to explore hidden web directories and resources?
We can see what’s currently installed on Kali as we did before by searching /bin/ for the term "bust"
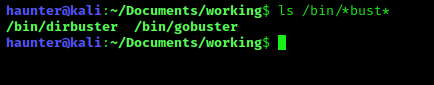
There are two options here:
dirbustergobuster
There are of course more options that are popular as well. For this lab, however, the answer will be gobuster.
Task 6
What switch do we use to specify to gobuster we want to perform dir busting specifically?
Let’s check with man gobuster WAIT VAT ZE FECK?
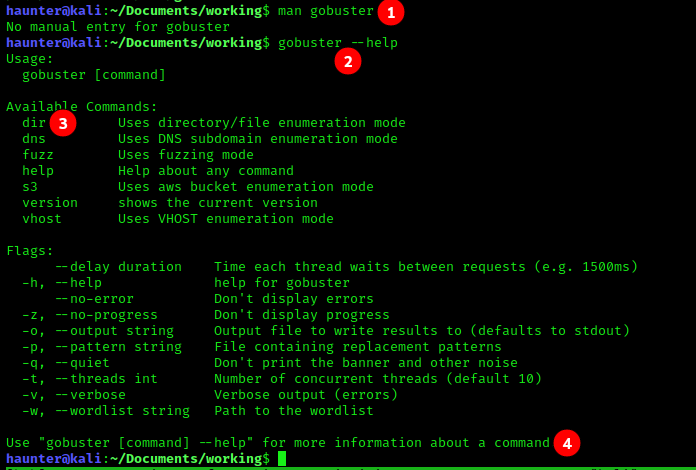
gobusterdoesn’t have a man page! :(- Luckily,
--helpis always a viable alternative. You can also reference this site for man pages for tools. - Now that we can see the tool’s syntax, we see that
diris the switch we need to include in our command for dir busting. - Take note that we can get specific command syntax with the formatting listed here. Example,
gobuster dir --helpwill get you the specifc help page with additionaldirdetails (see below image).
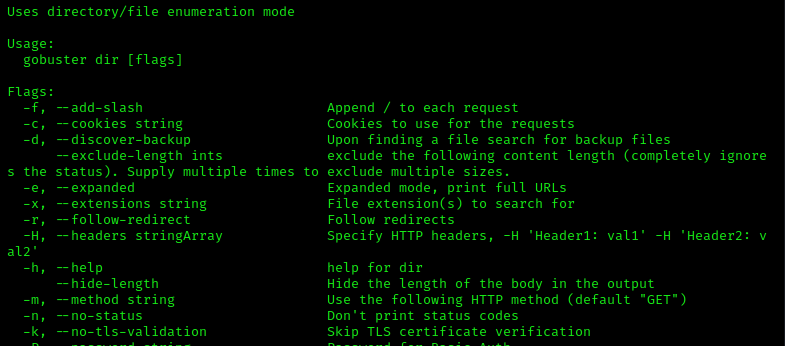
Task 7
What page is found during our dir busting activities?
Now for the fun stuff. First, here’s our command syntax per the man page:
gobuster dir -u $target -w path/to/wordlist
What the fuck is a wordlist?
As the name may suggest, they are precompiled files full of words that can be used in automated recon and/or bruteforce tools.
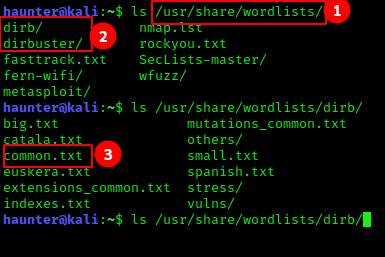
- Wordlists that are included in Kali are located in
/usr/share/wordlists. - There are different lists for different enumeration types or attacks. The two outlined here seem dir busting specific, so we will use lists from these. We will choose
dirbfirst, for reasons. - Within
/dirb, there are several wordlists.common.txtseems like a good first candidate.
Now that we have our wordlist picked, our revised command should look like this:
gobuster dir -u $target -w /usr/share/wordlists/dirb/common.txt
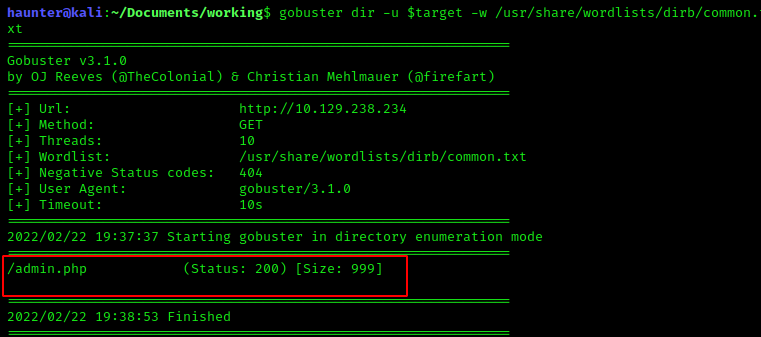
gobuster ran and found /admin.php.
Task 8
What is the status code reported by gobuster upon finding a successful page?
The above image shows that status code 200 indicates the specified page was found.
Task 9
Submit root flag
Capturing the Flag
We now know two key pieces of intel:
TARGEThosts a webserver onTCP/80. That means we can use a web browser to view pages.- We know that there is a login page at
TARGET_IP/admin.php. Sounds promising.
We navigate to the default landing page (enter the host’s IP in the browser bar).
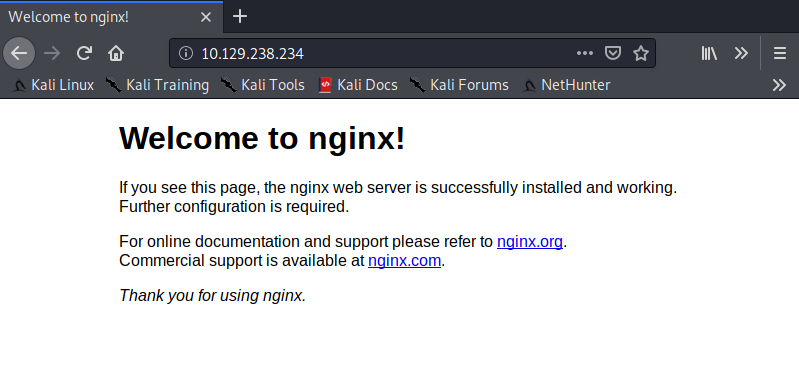
The above landing page is a default page for this webserver. This can indicate the webserver hasn’t been configured too much yet…meaning there could be default configurations we can exploit.
Let’s go to the /admin.php page we discovered with gobuster. Add the pagename to the end of the IP in the address bar.
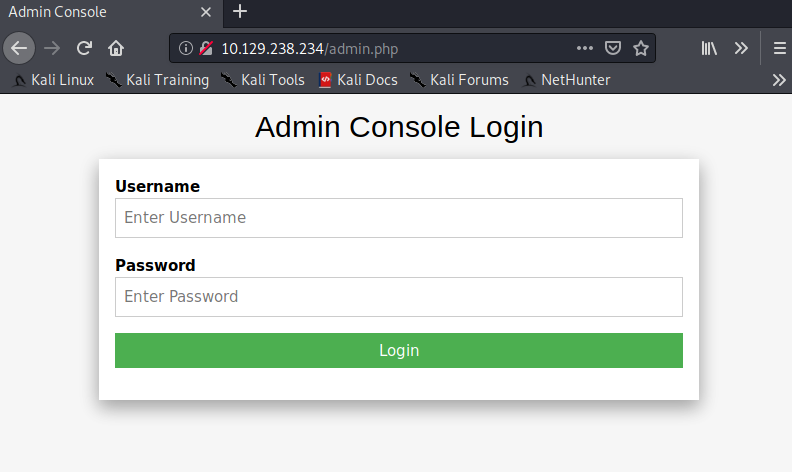
We have an admin login page.
Now there is a chance that default login credentials will work here. It seems like a simple server stood up without any changes yet.
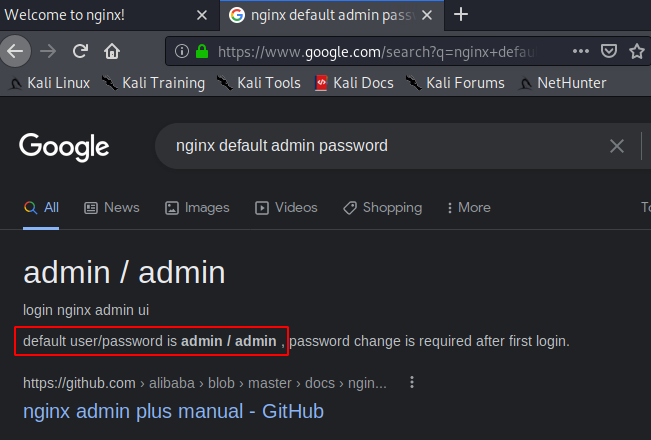
A quick search shows that default login creds for admin on nginx is admin/admin. Let’s try it :)
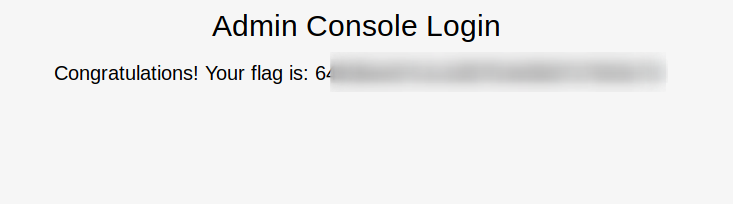
We have joy- default creds for admin let us right in. Grab teh flag & we have cleared Tier 0.

Lessons Learned
gobustercan be used to enumerate webservers for directories, pages, and moar. Login pages/admin consoles are HVTs- wordlists for dirbusting, password cracking, etc. can be found in
/usr/share/wordlists - search application documention or OSINT for default creds