Introduction
Explosion is the 4th 5th system (HTB keeps adding new machines) in the Tier 0 list, and the 1st of 2 VIP machines. RDP is the service theme here.
tl;dr
Spoiler!
1. The target is running a `RDP` server2. using `xfreerdp`, we get several informative errors. We learn that we need `/cert:ignore` and `/u:administrator`
3. Connection is successful and the flag is on the desktop
5.

Establishing a Connection
Spawn the bastard and get vpn going.
I’ve confirmed the target is reachable with a ping.
Initial Scan
nmap -v -T4 -A -oA recon/all $target 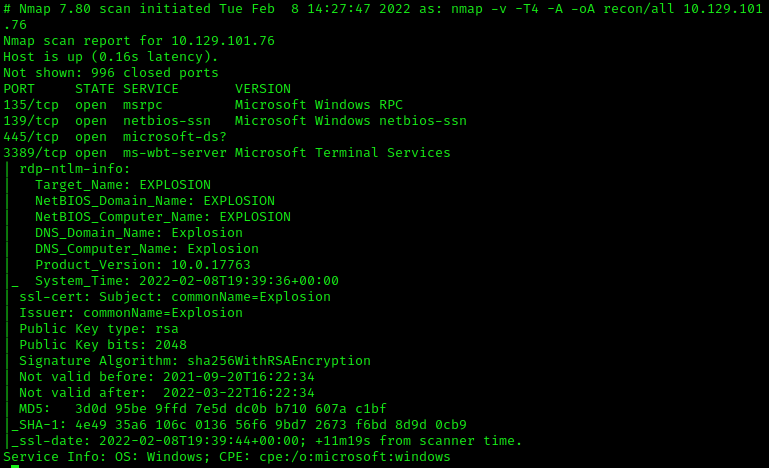
The Tasklist
Task 1
What does the 3-letter acronym RDP stand for?
RDP is short for Remote Desktop Protocol. You can read moar about RDP here.
Task 2
What is a 3-letter acronym that refers to interaction with the host through a command line interface?
Command Line Interface is abbreviated to cli. The terminal window seen in most of my screenshots is a cli (see-el-eye, not the thing your girlfriend says you can never find).
Task 3
What about graphical user interface interactions?
Similary, Graphical User Interface is abbreviated to gui (goo-ee, like that sock under your bed). Any program that utilzes preset menus / buttons in a visual manner, rather that terminal input, is using a gui.
Task 4
What is the name of an old remote access tool that came without encryption by default?
If you recall Meow, we used the telnet tool to connect to the target. telnet used to transmit data in-the-clear out of the box. Anyone that would be capturing packets would be able to see all data being transmitted…including passwords.
Task 5
What is the concept used to verify the identity of the remote host with SSH connections?
public-key cryptography
This is too complicated to cover here, so please reference the link here if you need a primer. Also note that this concept is not limited to just SSH, but many forms of secure connection types.
Task 6
What is the name of the tool that we can use to initiate a desktop projection to our host using the terminal?
I assumed this was installed on Kali, but didn’t know the name. A trick to find a tool that may contain some part you may know (“rdp” in this instance), is to search the /bin/ directory.
The /bin/ dir contains binaries (tools) , so we could run ls /bin/*rdp* to search for a possible tool.
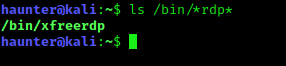
We found xfreerdp. This is our answer.
Task 7
What is the name of the service running on port 3389 TCP?
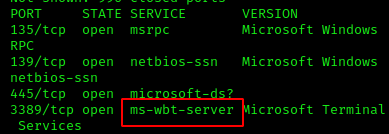
ms-webt-server
Task 8
What is the switch used to specify the target host’s IP address when using xfreerdp?
Open up the man page. man xfreerdp
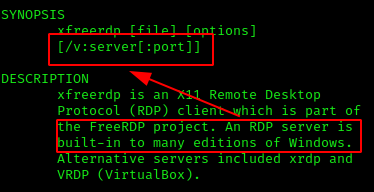
Right at the top we see the default command syntax. The /v:server[:port] portion seems promising. The terminology server is a bit off from host's IP address, but note Windows machines typically have a RDP server service built-in. That confirms this is the correct switch.
/v:
Task 9
Submit root flag
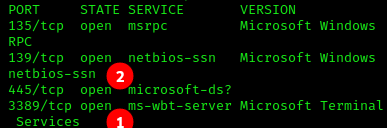
Based off our initial nmap scan, we know RDP(1) is open, but also SMB(2) on 445. Given that this machine is RDP oriented, this is unlikely to lead anywhere. However, it’s good practice to explore for a glaring opening, and also reinforce what we learned in previous lessons.
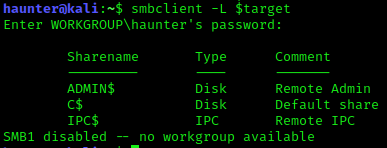
As we thought, dead-end. No shares to plunder. On to RDP.
Capturing the Flag
Let’s try a simple connection to see if we get lucky. We will use the default values besides specifying our target server so we do not need to specify port.
xfreerdp /v:$target
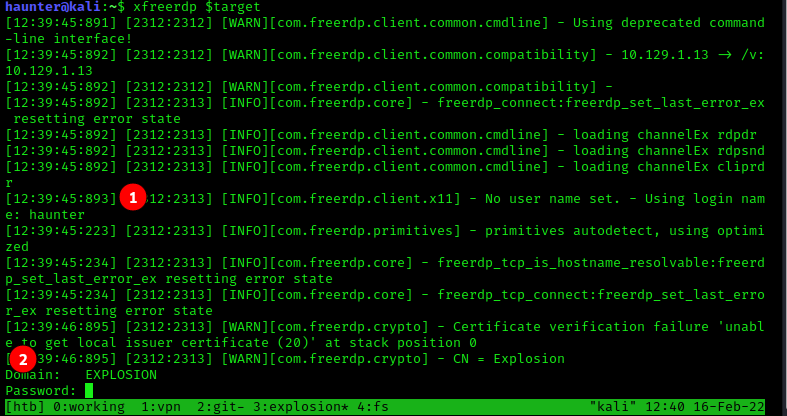
A connection attempt is initiated. Two things to note:
- As a username was not specified, the
RDPsession is trying to log us on the target system using our local usernamehaunter. I doubt this will work without specifying an account that would be found on the target system. - we are prompted for
DOMAINandPASSWORD.
Let’s check back to our scan results.
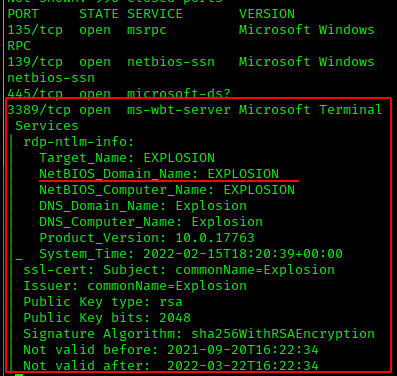
The DOMAIN is listed here as EXPLOSION. Let’s enter that but leave our password empty.
When we enter the info we get a lot of log data and the command terminates. There is too much info at once to easily parse.
We’ll take this time to create a log file and try again to see if we can get some insight on what went wrong.
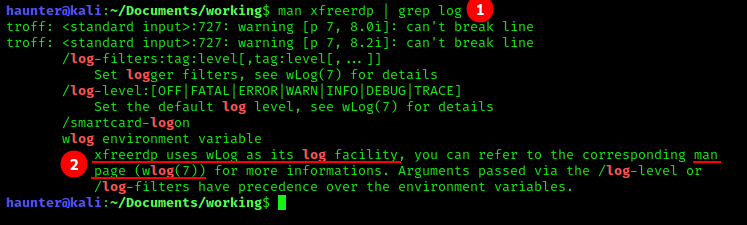
- We check the man pages for any built-in logging facilities with
man xfreerdp | grep log. - It looks like
xfreerdpuses something calledwlogto do so, and it actually tells us to runman wlogfor details.
After reading the man page, we learn that we need to prepend the xfreerdp command with some values. They are the following:
WLOG_APPEND=file*This tells wlog what we are to output the log to.WLOG_LEVEL=ERROR*This says to print log infos at the ERROR level and below (see the man page for details). Error messages should tell us what broke the connection attempt for us to fix.WLOG_FILEAPPENDER_FILE_PATH=./*This is the path to our log file. Using current working directory here.WLOG_FILEAPPENDER_FILE_NAME=output.log*The name of our log file.
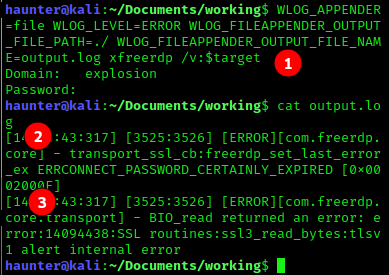
- The command now reads as
WLOG_APPEND=file WLOG_LEVEL=ERROR WLOG_FILEAPPENDER_FILE_PATH=./ WLOG_FILE_APPENDER_FILE_NAME=output.log xfreerdp /v:$target. We run the command and then output the contents. There are two ERRORS:
ERRCONNECT_PASSWORD_CERTAINLY_EXPIRED- We saw earlier that because we did not specify a user in the command, the session was attempting to log us into the remote target using our local user
haunter. This error is likely a result of that as the account does not exist on the target or in theEXPLOSIONdomain. We’ll need to specify a user next time. The man page shows that the/u:USERNAMEflag will allow us to specify a user to login with.
- We saw earlier that because we did not specify a user in the command, the session was attempting to log us into the remote target using our local user
SSL routines:ssl3_read_bytes...- This looks like a certificate issue. Teh googles suggest trying the
/cert:ignoreflag to remedying this issue.
- This looks like a certificate issue. Teh googles suggest trying the
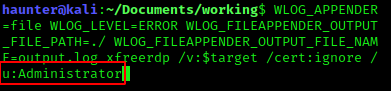
Now our revised command reads as follows:
WLOG_APPEND=file WLOG_LEVEL=ERROR WLOG_FILEAPPENDER_FILE_PATH=./ WLOG_FILE_APPENDER_FILE_NAME=output.log xfreerdp /v:$target /cert:ignore /u:Administrator
Note: I tried a few different default/built-in account names that Windows machines have baked in. In this instance, Administrator worked (see below) without a password.
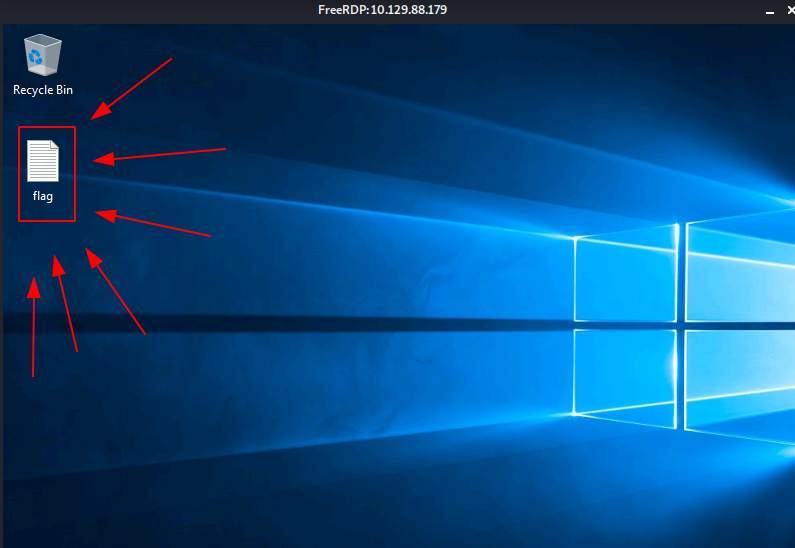
Upon executing the command, we got in and we can see the flag on the desktop. With that, we can wrap this one up after submitting the value.

Lessons Learned
xfreerdpcan be used forRDPfootholds.WLOGfacilities can be used to help troubleshoot connection issues